Secret Scanner Documentation
Overview
Secret Scanner is a feature designed to scan for secrets such as API keys, credentials, or sensitive data in your KeyRunner files. Once scanned, the secrets will be displayed on the UI, allowing you to manage and mitigate any potential security risks.
Features
- Scans for secrets such as API keys, tokens, passwords, etc.
- Displays identified secrets in a user-friendly interface.
- Regular scanning support to maintain up-to-date results.
Steps to Use the Secret Scanner
1. Open the Scanner Screen
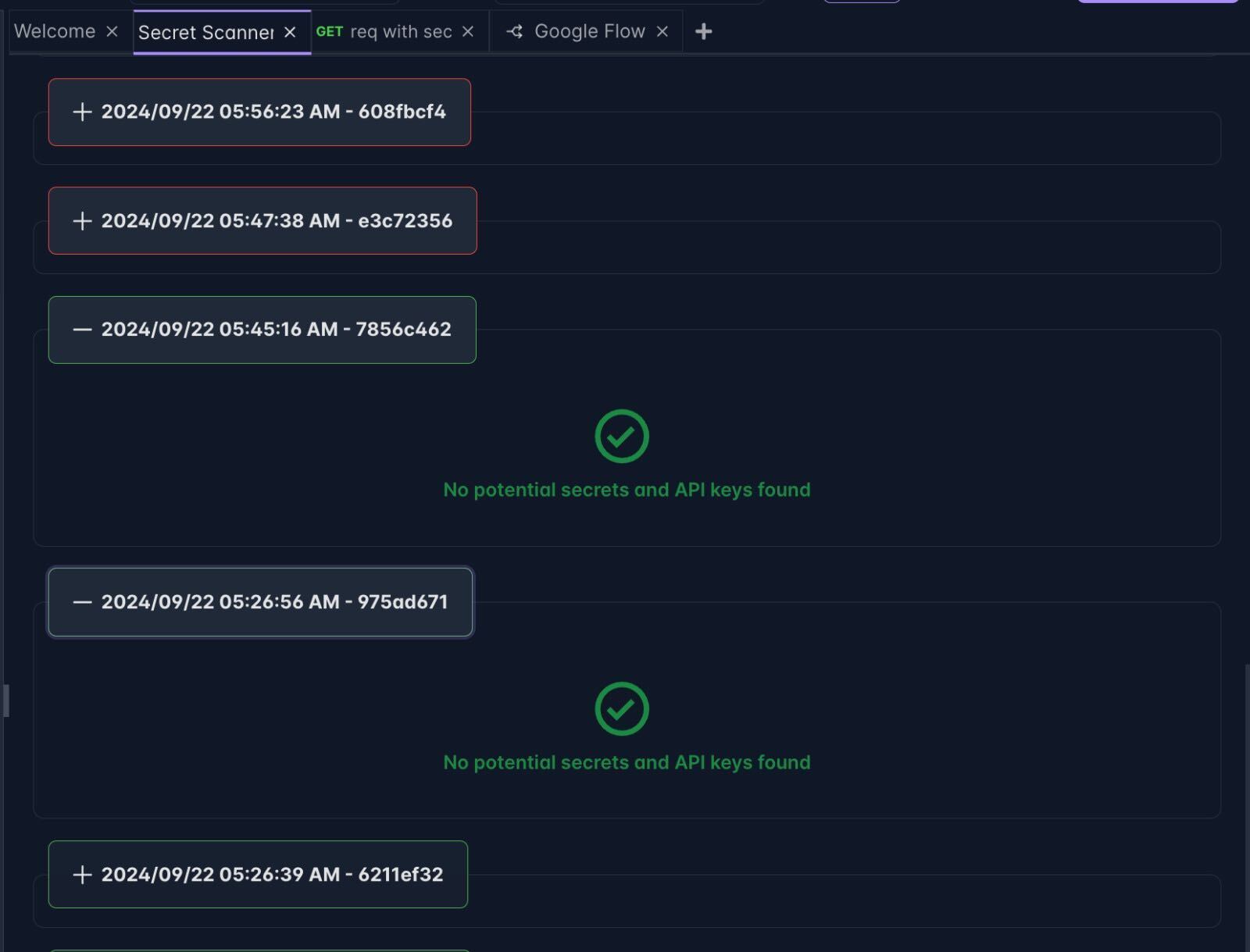
- Navigate to the Secret Scanner section from the footer.
- The screen will display previous scan results if any, and allow you to initiate a new scan.
2. Start a New Scan
- Click the Start Scan button to initiate a new scan of your workspace.
- The scanner will automatically detect and flag secrets based on predefined patterns for common sensitive data such as API keys, access tokens, and credentials.
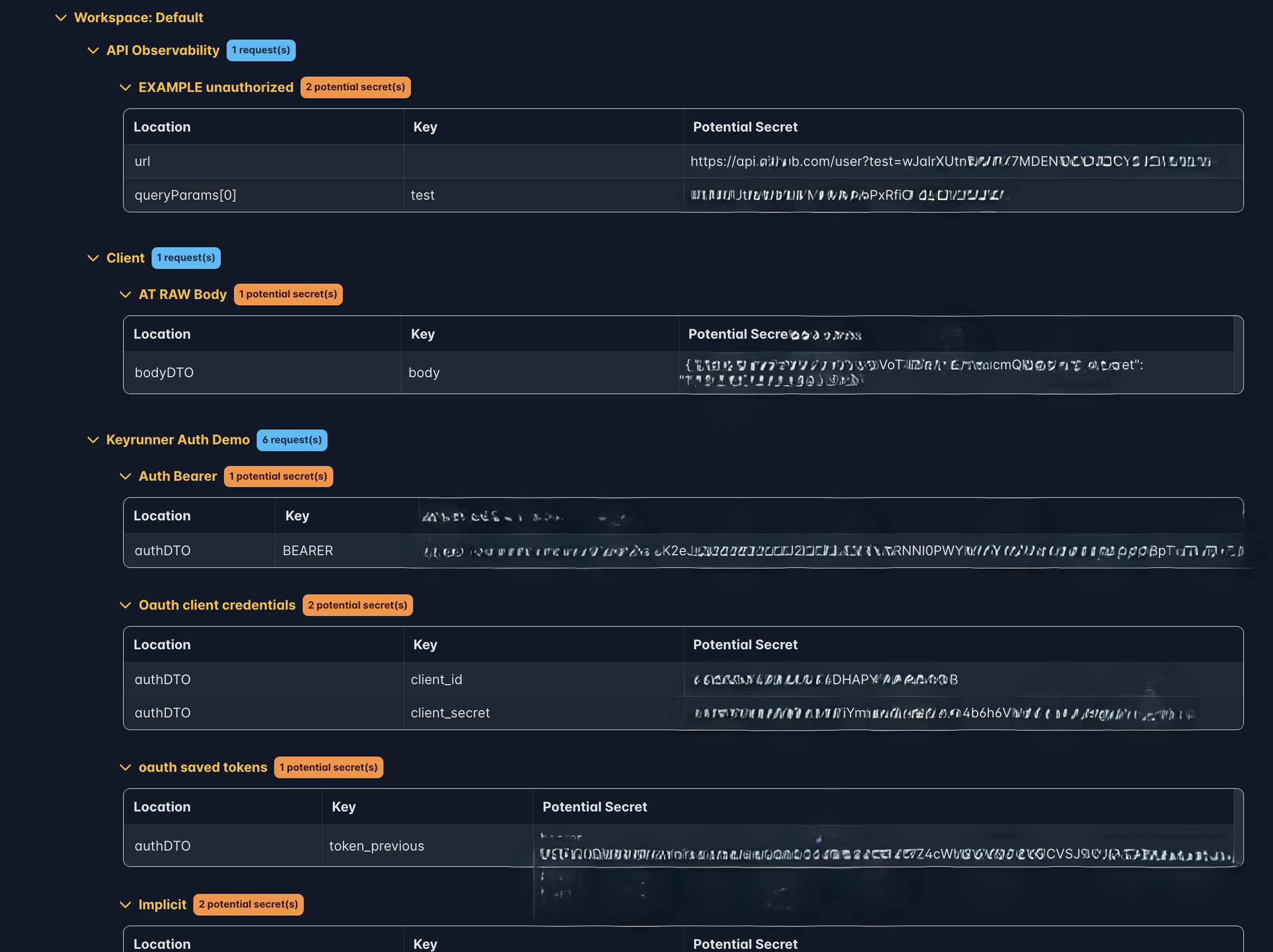
3. View Scan Results
- Once the scan is complete, the results will be displayed in a table on the UI.
- Type: Indicates the type of secret detected (API key, password, token, etc.).
- Location: Shows the request,collection or request flow where the secret was found.
- Risk Level: Assesses the potential risk (low, medium, high) based on the sensitivity of the secret.Future Release
- Actions: Options to ignore, mark as safe, or take remediation steps (e.g., revoking the key).Future Release
4. Remediation Options
- For each identified secret, you can take one of the following actions:
- Ignore: Mark the secret as not relevant (will not show in future scans).Future Release
- Mark as Safe: Confirm that the secret is safe (e.g., not in use).Future Release
- Remediate: Take actions such as storing them as environment variables, storing in vault and accesing them, revoking API keys or rotating credentials to ensure they are no longer vulnerable.
5. Export Results
- Click on the Export button to download the scan results as a CSV or JSON file for further analysis or sharing with security teams.Future Release
Additional Information
- Regular Scans: To ensure your workspace is secure, the scanner can be set to run periodically or triggered manually.Enterprise Feature
Future Features
We are planning to add the following features in future releases:
- Custom Patterns: You can customize the scanner to search for additional secret patterns by modifying the configuration file.
- Real-time secret scanning on file changes.
- Alerts and notifications for newly identified secrets.
- Allows exporting of results for further analysis.
FAQ
1. What types of secrets does the scanner detect?
The scanner detects API keys, access tokens, passwords, database credentials, and other sensitive data based on common patterns.
2. Is my scanned data stored anywhere?
yes, the scanned results are stored in your local machine where collections and requests are stored (\User\globalStorage\keyrunner-lite-by-liam\secretScanResults)
3. How can I request new features?
Please contact our support team or submit a feature request via our GitHub repository.
