Request Validator (OWASP API Top 10)
KeyRunner’s Request Validator helps you identify potential API security issues before you even send the request. It's designed to raise awareness and guide developers toward best practices aligned with the OWASP Top 10.
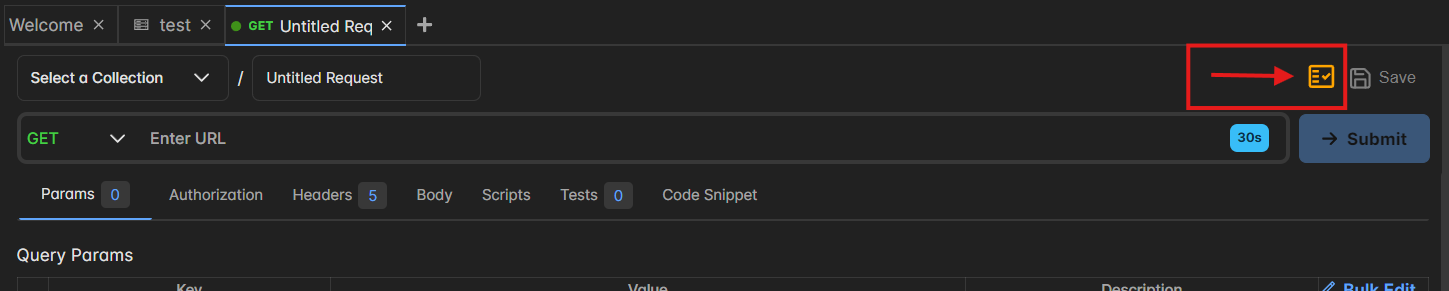
🛠️ How It Works
Available as a button on the Request screen
When clicked, it analyzes the current request
Checks for potential issues based on OWASP guidelines
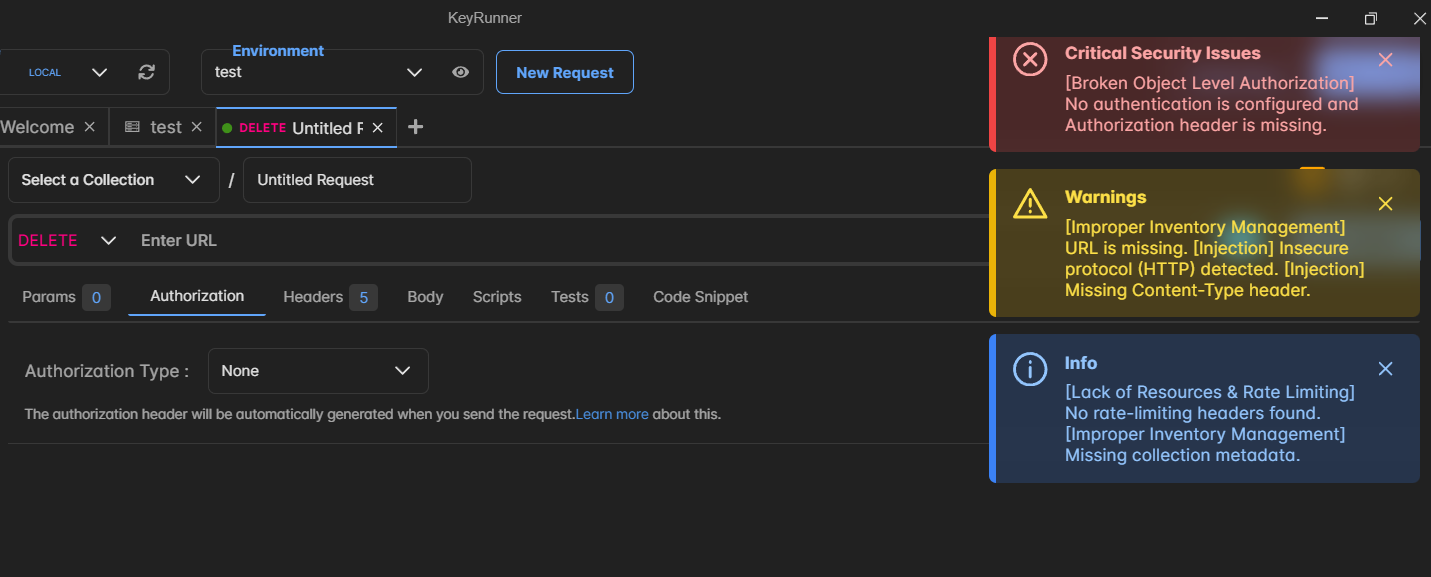
Results are shown as toast notifications categorized by severity:
- ℹ️ Info: Suggestion or best practice
- ⚠️ Warning: Something potentially risky
- ❗ Critical: High-risk vulnerability or misconfiguration
🔍 OWASP Top 10 Coverage
The validator scans requests for patterns or practices that may relate to the following OWASP categories:
| OWASP Category | What It Detects |
|---|---|
| A01 - Broken Access Control | Missing or weak Authorization headers, overly permissive endpoints |
| A02 - Cryptographic Failures | Sending credentials or tokens over non-HTTPS, weak encryption usage |
| A03 - Injection | SQL, NoSQL, or command injection patterns in query/body headers |
| A04 - Insecure Design | Unsafe HTTP methods (e.g., PUT, DELETE without auth), open CORS configs |
| A05 - Security Misconfiguration | Missing headers (X-Content-Type-Options, X-Frame-Options), exposed stack traces |
| A06 - Vulnerable & Outdated Components | Coming soon: flag known vulnerable headers or libraries (planned enhancement) |
| A07 - Identification & Authentication Failures | No or weak Authorization headers, missing Authentication method in sensitive requests |
| A08 - Software & Data Integrity Failures | Detects use of unsigned or unchecked payloads (planned enhancement) |
| A09 - Security Logging & Monitoring Failures | Planned: Suggestions on logging tokens or sensitive values in request bodies |
| A10 - SSRF (Server-Side Request Forgery) | Use of internal IPs, open redirection patterns in request bodies or params |
We're constantly evolving this list and will expand detection as feedback grows.
🔁 Re-check Anytime
After resolving issues flagged by the validator, click the button again to run a new scan. It will re-validate the updated request.
✅ No need to reload or reset — it's designed to be fast and frictionless.
🧪 Beta Notice
This feature is currently in beta.
- It will expand to cover more OWASP categories over time
- We'd love your feedback — use the support panel or drop us suggestions
KeyRunner’s Request Validator is built to help developers catch risks early right where they work and evolve API hygiene without slowing things down.
